How is anonymization handled for sensitive data?
Data Anonymization
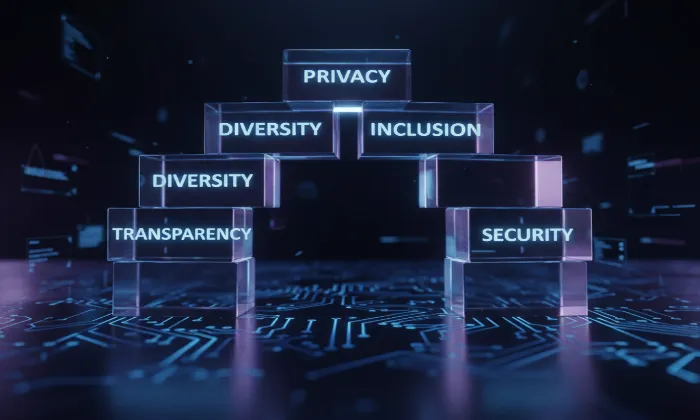
Privacy
Data Protection
Ensuring the privacy and security of sensitive data is paramount, particularly in the healthcare sector. At FutureBeeAI, we understand the critical need for anonymization in datasets, especially those involving simulated doctor-patient interactions. Here’s how we handle anonymization to protect sensitive data while maintaining the integrity and utility of our datasets.
The Importance of Anonymization
Anonymization in datasets is crucial to prevent unauthorized access to personal information. It allows organizations to use and share data for research and development without compromising individual privacy. This is especially significant in healthcare, where data sensitivity is high, and regulations like GDPR and HIPAA govern the use and sharing of personal information.
Our Anonymization Process
- Simulated Conversations: The Doctor–Patient Conversation Speech Dataset is built on simulated interactions, where no actual patient information is used. Conversations are crafted under the guidance of licensed physicians, ensuring realistic clinical scenarios without real patient identifiers.
- Data Masking and Replacement: Any potential identifiers, such as names or locations, are replaced with placeholders or anonymized tags (e.g., [NAME], [LOCATION]).
- Audio and Transcript Management: In audio recordings, any accidental mention of personal data is masked with a beep. Transcripts undergo thorough review to replace personal identifiers with anonymized tags. This dual-layer approach ensures both audio and text data remain secure.
- Ethics and Compliance Oversight: An independent ethics and compliance review panel oversees all healthcare data projects, ensuring adherence to privacy laws like GDPR and HIPAA. This panel ensures that our anonymization methods are robust and up-to-date with global standards.
- Informed Consent and Simulation: All contributors provide explicit informed consent before participating. By using simulated dialogues, we eliminate the risks associated with capturing genuine patient data, while still offering high-quality, realistic datasets for AI training.
Why Simulated Data is Effective
Simulated datasets like ours offer significant advantages by balancing realism with privacy. They allow for the creation of linguistically and contextually rich data without the ethical and legal challenges of using real patient information. This approach enables AI systems to be trained on data that mirrors real-world interactions, ensuring they are effective and reliable when deployed in healthcare environments.
FutureBeeAI’s Commitment
At FutureBeeAI, we are committed to setting high standards for data privacy and security. Our rigorous anonymization processes and ethical oversight ensure that our datasets are both valuable and safe to use. By choosing FutureBeeAI, AI engineers, researchers, and product managers can confidently develop healthcare AI systems that respect privacy while delivering cutting-edge performance.
FAQs
Q. How does FutureBeeAI ensure the authenticity of simulated data?
A. FutureBeeAI collaborates with licensed physicians to design clinical scenarios, ensuring the conversations are medically accurate and reflective of real-world interactions.
Q. Can clients request additional anonymization features?
A. Yes, FutureBeeAI offers customizable annotation layers and can implement additional anonymization measures based on client needs, ensuring flexibility and security for specific use cases.
What Else Do People Ask?
Related AI Articles
Browse Matching Datasets
Acquiring high-quality AI datasets has never been easier!!!
Get in touch with our AI data expert now!